Investigate the dangers and threats that continue to exist around cyberspace around users (Part 1)
- Adware: The nature of these malware is simply to send advertising messages and make money to their creators. The default design of these software is to inadvertently display messages with promotional content on the user's screen. Such malware is often visible in browsers, but it works well in mobile applications that users download and install as free (such as filtering). The creators of these malware are trying to persuade the user to install it so they can design its appearance as legitimate software or combine its software with a widely used software and provide users with the original software name.
Here are some examples of the symptoms and behaviors of these malware in the system:
- Ads appear with content that has nothing to do with the software function used.
- The Browser homepage mysteriously changes without the user's permission.
- Frequently visited web pages are not displayed properly.
- The user clicks on a particular website link but is redirected to an unexpected and unrelated page.
- The user's operating system starts automatically installing unwanted software.
- The browser crashes regularly.
- Ransomware: ransomware, is an example of malware that prevents users from accessing their files by locking the device as well as encrypting the files and forcing them to pay for their files. Some examples of messages that appear on infected systems:
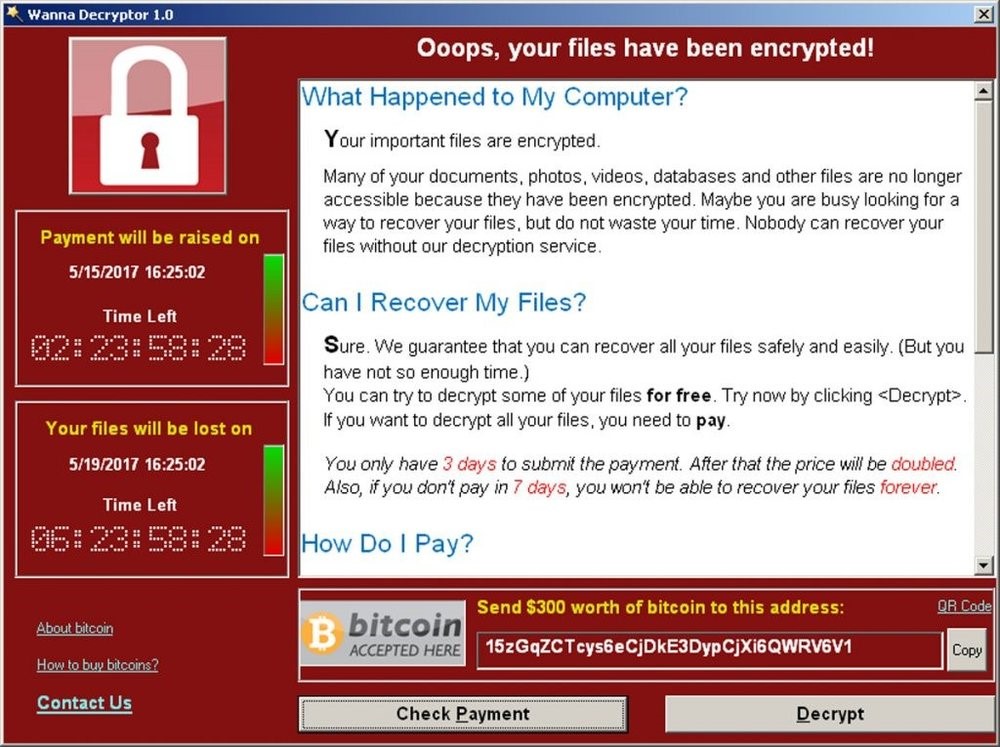 Ransomware can infect systems in different ways. One of the most common ways to infect systems today is to send links, malware, pdf files or even word files via spam emails.
Ransomware can infect systems in different ways. One of the most common ways to infect systems today is to send links, malware, pdf files or even word files via spam emails.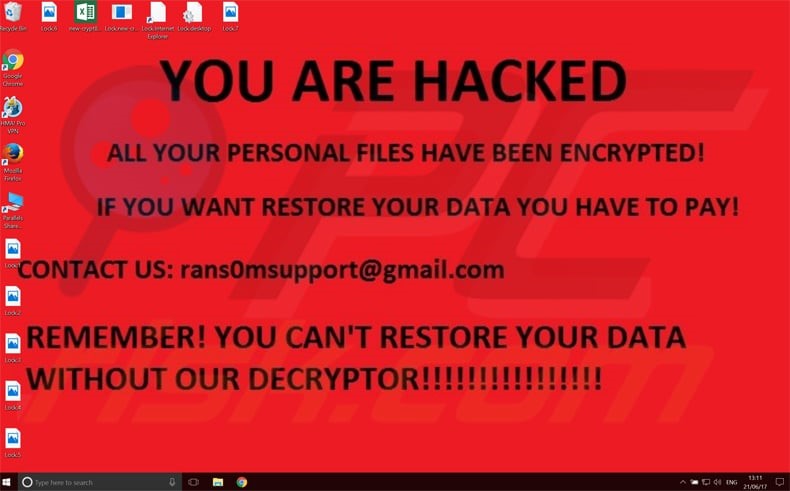
Ransomware category:
Scareware:
The user may receive a pop-up message claiming that the malware has been transmitted to his system and the only way to get rid of it is to pay (or pay) the ransom, and possibly continue using it if he does not pay. Bomber from pop-ups, but files are safe.

Screen Locker:
The ransomware appeared at the beginning of the system by locking the screen, often accompanied by fake content from the official FBI or US Department of Justice, saying illegal activity was detected on your computer and you should be fined.

Encrypting Ransomware:
This category is the most dangerous type of ransomware because it captures and encrypts files on the system and requests payment and ransom for decrypting users. The reason this type of ransomware is dangerous is that after encryption on files, no security software can recover the password. In this case, paying a fee is not a reasonable move as there is no guarantee that the attacker will recover the files.

If you see the above symptoms and the like in your system, you can take steps to fix the problem. First, back up your files regularly. You can clean your system using a variety of tools, which we will review below:
- Malwarebytes
Malwabytes is software that can be used to search for and remove annoying advertisements, PUPs (programs that display the ability to display messages with advertisements on a topic unrelated to the downloaded software, and often these programs Combined with widely used software) and new types of malware in the system. Free as well as subscriptions (through subscription purchases) are also supported on operating systems such as Windows, Mac, Android, ios and even Chromebooks. This software, in addition to the ability to scan, detect and remove malware, activates automatic protection status in the system, which prevents the system from being infected.
The following is a download link for various operating systems:
Download link for Mac OS
Download link for Android OS
Download link for ios
Download link for chromebook OS - MalwareFox
Feature check:
- Anti-Adware: This app has modules to remove advertising messages and also prevents the user from redirecting to unwanted and unrelated pages by enabling automatic protection of this program.
- Ransomware Protection: Enables automatic ransomware protection to prevent system ransomware from being infected.
The following is a download link for various operating systems:
Download link for Windows OS
Download link for Windows Android